Verify Server Cert Option
Notice:
This is a very important option for data security, so please do not disable it unless you clearly understand the implications.
If you have any questions about this option, please contact us.
Advanced Configuration: Verify Server Cert
On the Add Account page, click the corresponding Advanced button to open the Advanced Settings dialog, as shown below:
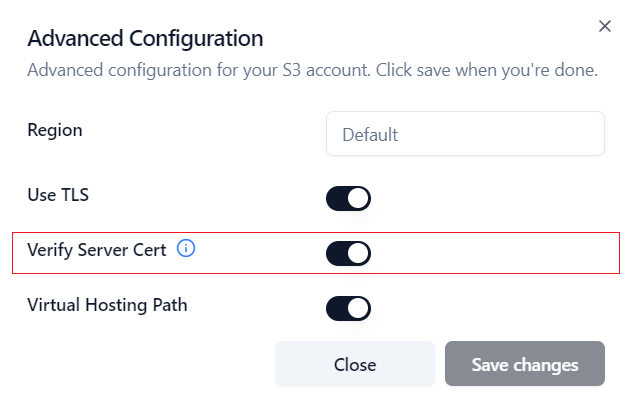
When should I enable the option?
When you use S3 Explorer to connect to common and well-known S3 providers, you will NOT need to turn this off most of the time. You should always keep it on!
This option is on by default.
Common and well-known S3 service providers mentioned here include but are not limited to:
- Amazon S3
- Aliyun OSS
- Tencent COS
- Huwei OBS
- Other well-known S3 service providers not listed here
Because their server certificates are always signed by well-known CA, they should be trusted by default on your platform (Window, Linux, macOS).
So keep it enabled and you should be able to successfully connect to the server. This is why it is enabled by default
When should I disable the option?
Usually you need to turn this option off to connect to your S3 server when you are in the following scenarios:
- You or your company have built a corresponding S3 server, but it is used internally or as a test server.
- You deployed the MINIO server yourself.
- The OS you are using is too old, resulting in the system's built-in CA certificate not being updated in time,
causing the corresponding server certificate to be untrusted by the current system.
- For Windows: It is possible that you are using a very old system and Microsoft no longer provides updates.
- For Linux: The CA certificate that comes with OpenSSL on your system is too old.
n the above situation, if you keep the option enabled, you may encounter an error message saying "Cannot connect".
S3 Explorer reports a message similar to: Error verifying server certificate.
In order to connect to the S3 server properly, you need to disable this option to successfully connect to the server.
What does disabling this option mean?
Disabling this option will put your data at great risk.
Here are some possible hazards:
1. Man-in-the-Middle, MitM
This is the most immediate and serious risk. The fundamental purpose of certificate verification is to ensure that you are communicating with the server you claim to be connecting to. If you disable certificate verification, an attacker can establish a proxy connection between you and the server and pretend to be the server.
- Attack process The attacker intercepts your connection request and sends you a forged certificate. Since you have disabled certificate verification, your client accepts the forged certificate and establishes an encrypted session. Meanwhile, the attacker establishes a connection to the real server.
- Result: Attackers can decrypt, view, and modify all the data you send (such as usernames, passwords, personal information, credit card numbers, etc.), and then re-encrypt and send it to the server. The content of your communication will be completely exposed to attackers.
2. Identity Spoofing
A certificate is a digital proof of a server's identity. If a client doesn't verify the certificate, it can't be sure of the server's true identity. Attackers can create a malicious website or service with a domain name that closely resembles a legitimate service and trick users into connecting. Disabling certificate verification makes this type of deception easy.
3. Data Integrity Risk
While the TLS/SSL protocols themselves ensure encryption and integrity of data during transmission, if the server's identity is forged by a man-in-the-middle, an attacker can tamper with session keys or inject malicious content into the data during transmission. Since you can't trust the other end of the connection, the data can be tampered with before it can be "securely" encrypted.
4. Trust Chain Breakage
The normal certificate validation process checks a complete chain of trust: the client trusts the root certificate authority (CA), which signs the intermediate certificate, which in turn signs the server certificate. Disabling certificate validation completely bypasses this trust model. This allows any self-signed or invalid certificate to be accepted, making it easy for attackers to deceive clients with a forged certificate.
5. Other security risks
Summary and suggestions
Disabling certificate verification is like trading blindly in a market full of scammers. Although you may eventually get the product (data), you have no idea who your counterparty is, nor do you know if they have tampered with your wallet (data) during the transaction.
Disabling certificate validation should only be considered in the following rare, special, and controlled circumstances:
- For testing and development environments only: During internal testing, you might need to connect to a server that uses a self-signed certificate and you know that no external attackers can intervene.
- The risks are clearly known and the operation is temporary: For example, when debugging a network problem, you need to temporarily eliminate certificate issues to locate the fault, but you must restore certificate verification immediately after debugging is completed.
In any production environment, public network or scenario where sensitive data is processed, You should never disable certificate validation. If the server certificate is invalid, you should find out why it's invalid (e.g., expired, domain name mismatch, incomplete trust chain, etc.) and fix it, rather than simply disabling security features.